Accidentally Committed Secrets on GitHub? Here's What to Do!
Accidentally committing sensitive credentials to your Git repository can have severe consequences. Leaked secrets—such as API keys, passwords, or internal tokens—can expose your systems to unauthorized access, leading to security breaches and potential financial losses.
Understanding the Risks
When a secret is committed to GitHub:
- Historical Exposure: Even if you delete the secret in a subsequent commit, Git's history retains the leaked data.
- Automated Scanners: Attackers and automated bots constantly scan public repositories for such leaks.
- Delayed Rotation: Delays in identifying and rotating compromised secrets can lead to prolonged exposure.
Immediate Steps to Take
- Revoke and Rotate the Leaked Secret:
Immediately invalidate the leaked credentials. Whether it's an API key, token, or password, revoke it and generate new ones. This is critical because—even if the secret is later removed from your code—the leaked version may have already been compromised. - Remove the Secret from Your Repository History:
Simply deleting the secret from your latest commit isn't enough—it still exists in Git history. You need to completely purge it. The following example will remove all occurrences ofYOUR_LEAKED_SECRETfrom your Git history using git-filter-repo:pip install git-filter-repo
# Will replace all occurrences of YOUR_LEAKED_SECRET with xxxxxxxx in your Git history
git filter-repo --replace-text <(echo 'YOUR_LEAKED_SECRET==>xxxxxxxx')
# Be aware that rewriting history requires force pushing, which can affect collaborators.
git push origin --force --all
Preventing Future Leaks
Use a Secrets Manager
There are many secrets managers on the market that you can use to safely store your secrets. However, most of them are complicated and difficult to work with.
Vault++ is a modern secrets management platform that makes secrets management simple and intuitive. It is packed with features such as secret rotation, audit logs, secret scanning, and more. If you are working in a team, you'll love the Reveal Request and Merge Request features that enable seamless collaboration.
Vault++ exports secrets as environment variables, requiring no SDK and supporting all platforms and programming languages. Below are examples of code after integrating with Vault++:
// Before
const AWS_ACCESS_KEY_ID = 'AKIAIOSFODNN7EXAMPLE';
// After
const AWS_ACCESS_KEY_ID = process.env.AWS_ACCESS_KEY_ID;
# Before
AWS_ACCESS_KEY_ID = 'AKIAIOSFODNN7EXAMPLE'
# After
import os
AWS_ACCESS_KEY_ID = os.environ['AWS_ACCESS_KEY_ID']
# Before
AWS_ACCESS_KEY_ID = 'AKIAIOSFODNN7EXAMPLE'
# After
import os
AWS_ACCESS_KEY_ID = os.environ['AWS_ACCESS_KEY_ID']
# Using magic %env
%env AWS_ACCESS_KEY_ID
// Before
String AWS_ACCESS_KEY_ID = "AKIAIOSFODNN7EXAMPLE";
// After
String AWS_ACCESS_KEY_ID = System.getenv("JAVA_HOME");
// Before
string AWS_ACCESS_KEY_ID = "AKIAIOSFODNN7EXAMPLE";
// After
string AWS_ACCESS_KEY_ID = Environment.GetEnvironmentVariable("AWS_ACCESS_KEY_ID");
Install a Pre-Commit Hook
The Vault++ pre-commit hook intercepts Git commits and scans for secrets before they are added to your repository. You can easily install the pre-commit hook into your new or existing Git repositories.
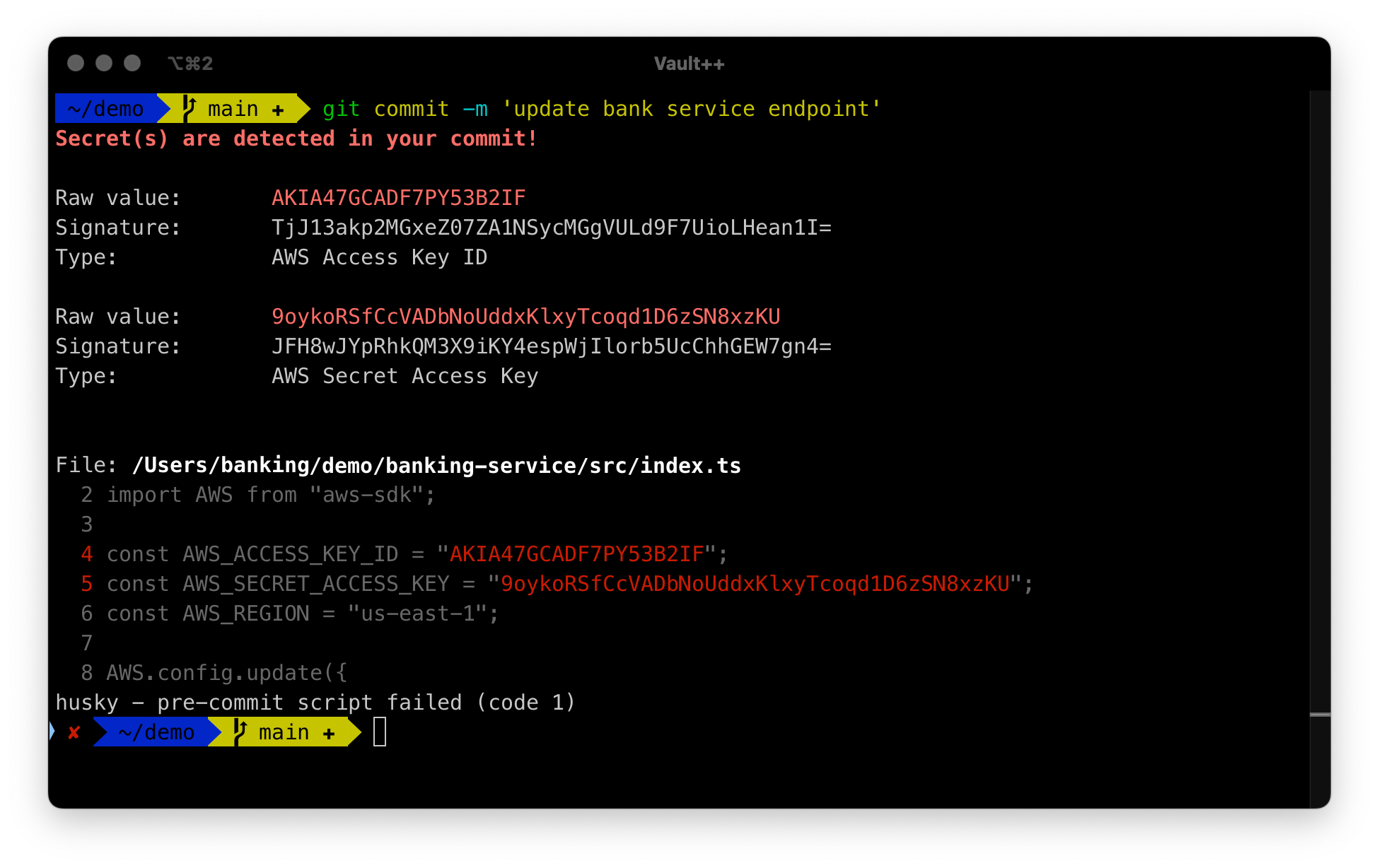
Get Vault++ for Free Today
By storing secrets in Vault++ and integrating Vault++'s pre-commit hook, you can prevent future leaks and maintain a robust security posture. The best part? Vault++ is free to use, making it an accessible solution for individuals and teams looking to secure their codebases.
Quickstart — ⏰ 5mContact Sales